Stijging actieve crypto-mining malware dankzij Bitcoin-hype
Het succes van Bitcoin en andere crypto-munten is niet alleen speculanten opgevallen, ook cybercriminelen willen een slaatje slaan uit de crypto currency-hype. Dat leidt tot een sterke stijging in crypto-mining malware.
Dat concludeert Check Point, die maandelijks een update geven van de meest actieve soorten malware binnen de Global Threat Index. December 2017 kende een flinke stijging in actieve crypto-mining malware. Deze malware richt zich op organisaties en gebruikt de resources van een geïnfecteerd systeem om crypto currencies te minen.
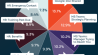
Top 10 most wanted malware
De maandelijkse lijst die Check Point uitgeeft geeft een beeld van de meest actieve malware in de gegeven maand. De eerste plek wordt ingenomen door Coinhive. Deze malware verzorgd online mining van de Monero crypto-munt. Coinhive heeft hiermee een behoorlijke impact op de prestaties van het geïnfecteerde systeem.
De gehele top 10 vind je hieronder:
-
Coinhive – Crypto-Miner designed to perform online mining of Monero cryptocurrency when a user visits a web page without the user’s approval. The implanted JavaScript uses great computational resources of the end users machines to mine coins, thus impacting the performance of the system.
-
Rig ek – Exploit Kit first introduced in 2014. Rig delivers Exploits for Flash, Java, Silverlight and Internet Explorer. The infection chain starts with a redirection to a landing page that contains JavaScript that checks for vulnerable plug-ins and delivers the exploit.
-
Cryptoloot – Crypto-Miner, using the victim’s CPU or GPU power and existing resources for crypto mining – adding transactions to the blockchain and releasing new currency. It is a competitor to Coinhive, trying to pull the rug under it by asking less percents of revenue from websites.
-
Roughted – Large scale Malvertising used to deliver various malicious websites and payloads such as scams, adware, exploit kits and ransomware. It can be used to attack any type of platform and operating system, and utilizes ad-blocker bypassing and fingerprinting in order to make sure it delivers the most relevant attack.
-
Fireball – Browser-hijacker that can be turned into a full-functioning malware downloader. It is capable of executing any code on the victim machines, resulting in a wide range of actions from stealing credentials to dropping additional malware.
-
Globeimposter – Ransomware disguised as a variant of the Globe ransomware. It was discovered in May 2017, and is distributed by spam campaigns, malvertising and exploit kits. Upon encryption, the ransomware appends the .crypt extension to each encrypted file.
-
Ramnit – Banking Trojan that steals banking credentials, FTP passwords, session cookies and personal data.
-
Virut – Botnet that is known to be used for cybercrime activities such as DDoS attacks, spam, fraud, data theft, and pay-per-install activities. It spreads through executable file infection (through infected USB sticks and other media), and more recently, through compromised HTML files (thus infecting vulnerable browsers visiting compromised websites)
-
Conficker – Worm that allows remote operations and malware download. The infected machine is controlled by a botnet, which contacts its Command & Control server to receive instructions.
- Rocks – Web based Crypto-Miner, which hijacks the victim’s CPU and existing resources for crypto mining.